Kakao Tech Bootcamp team project. Built and evolved the entire cloud infrastructure from a single VM to a fully orchestrated Kubernetes environment on AWS EKS with GitOps-based CI/CD pipeline.
Key Features
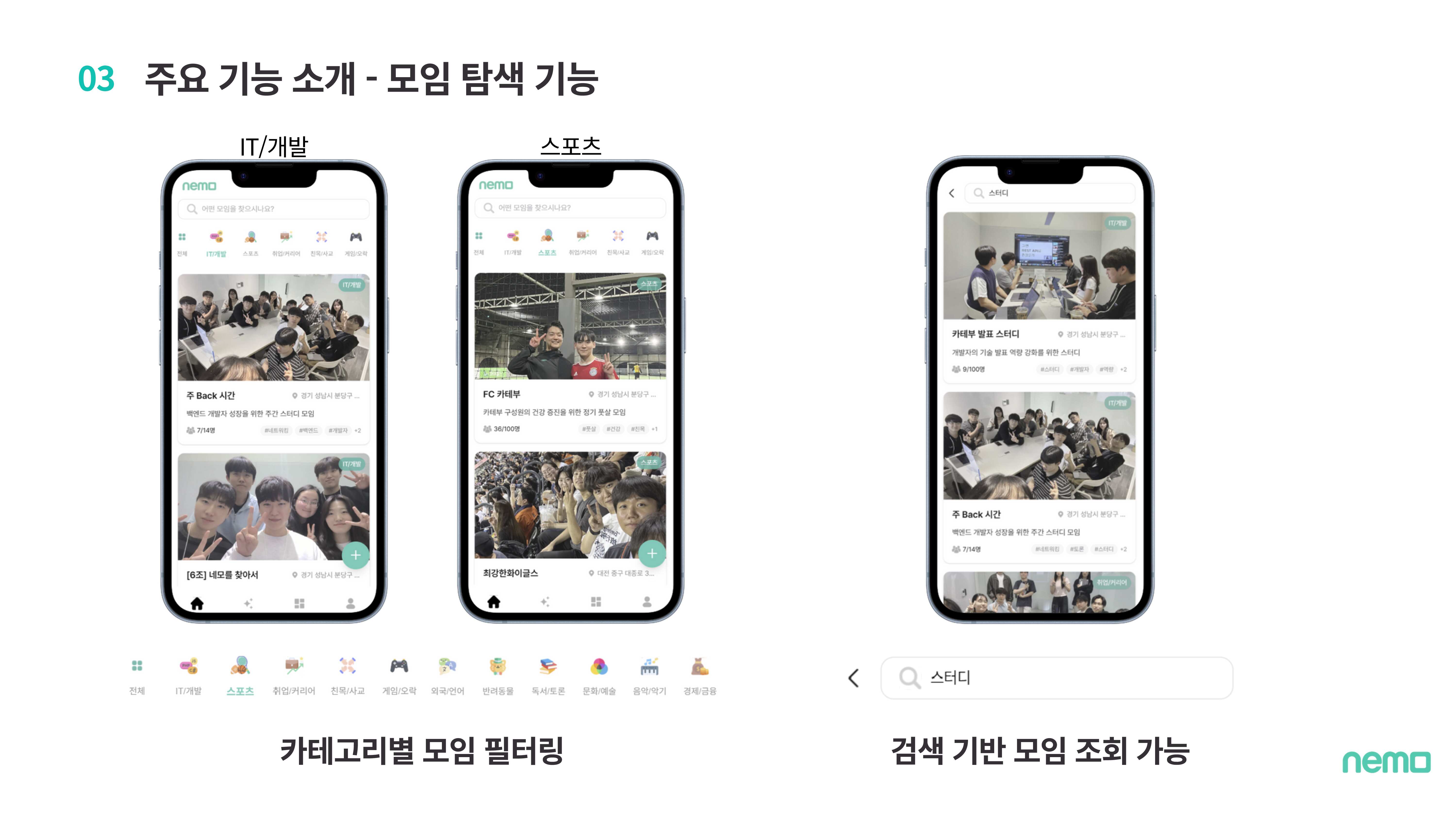
Category-based group filtering and keyword search
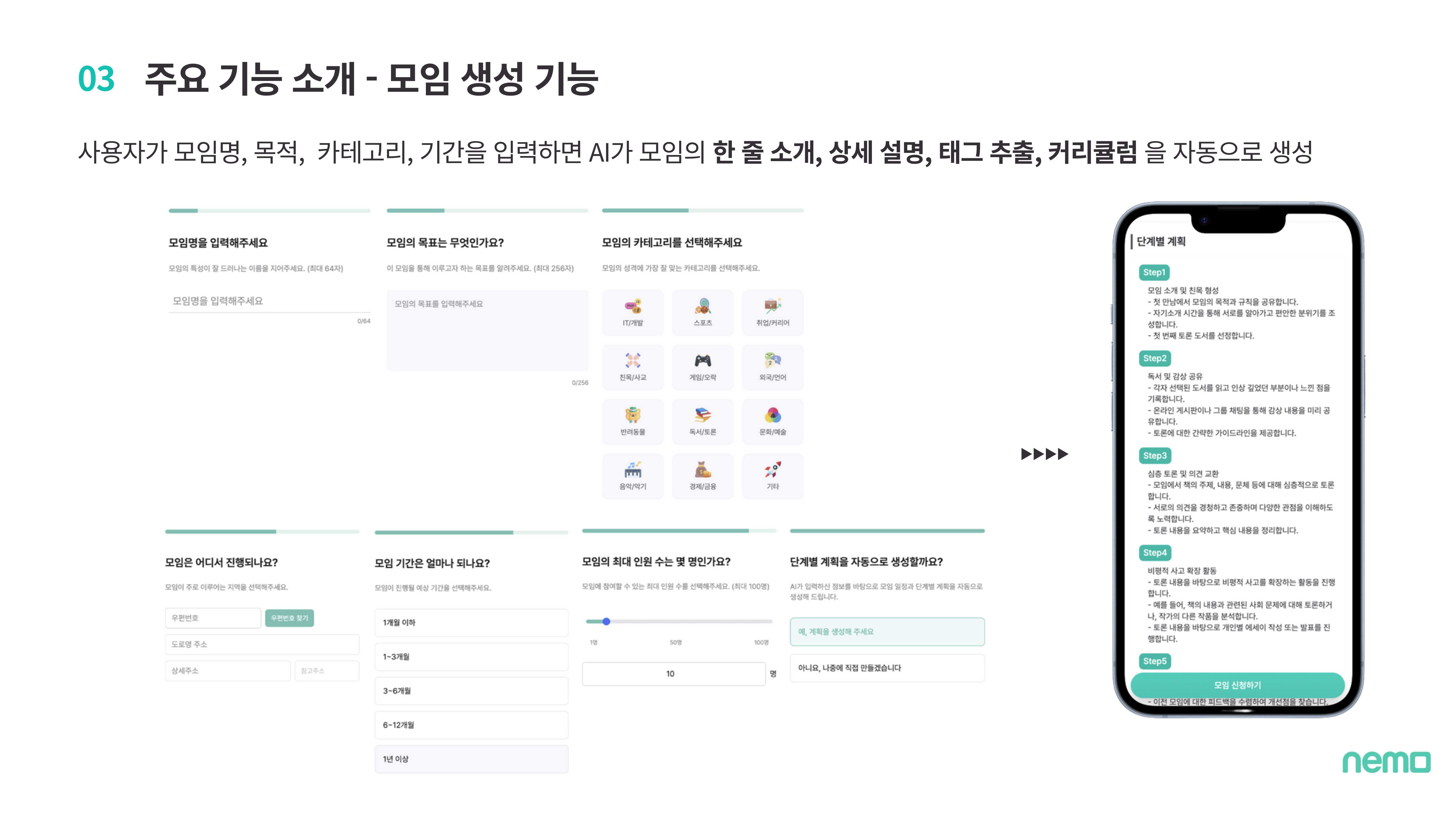
AI auto-generates group descriptions, tags, and curriculum from user inputs
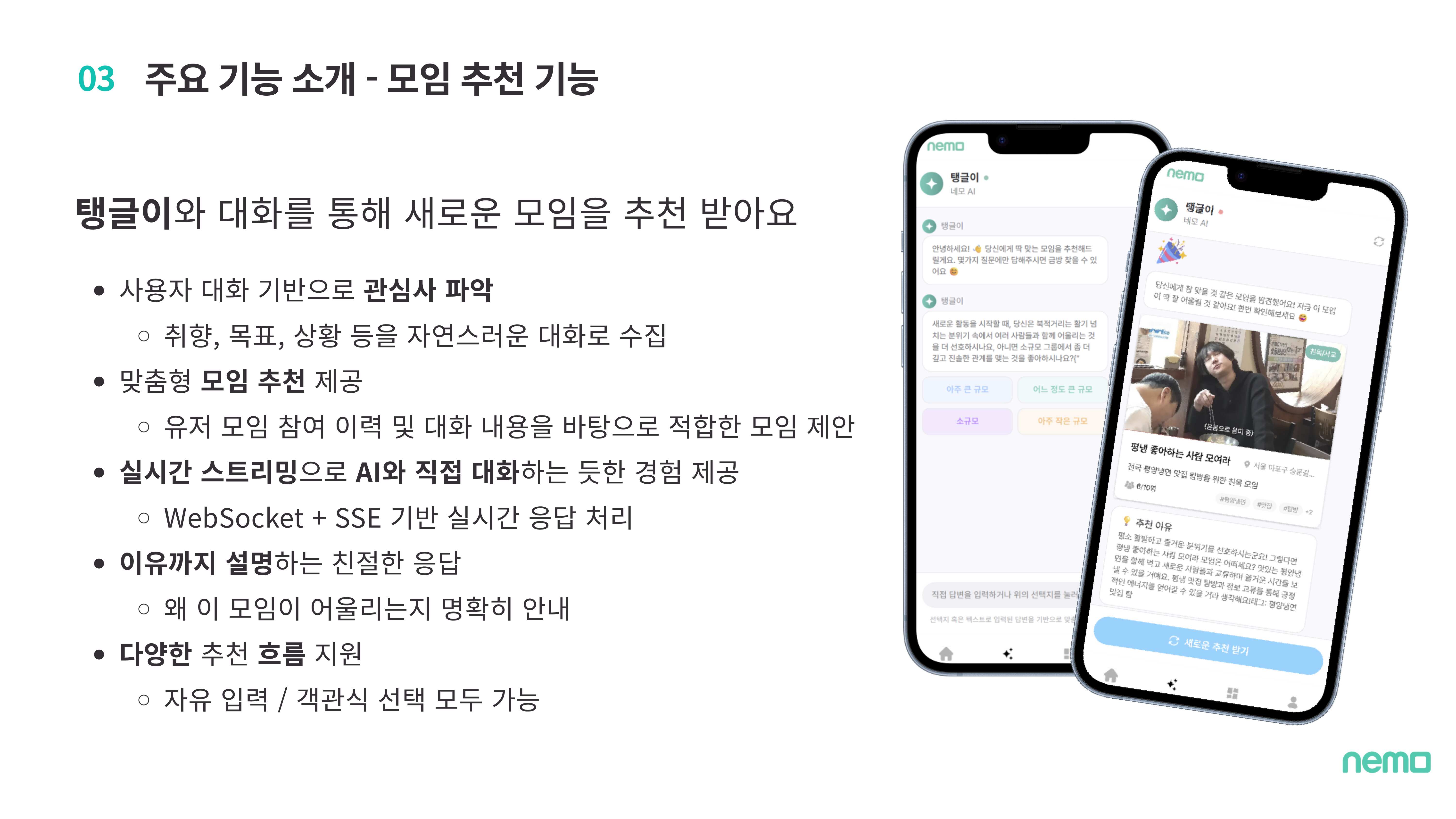
Conversational AI chatbot recommends groups based on user interests
Tech Stack (My Part)
My Contributions
PM2 manual deploy → Docker + CI/CD → EKS + ArgoCD GitOps
Cluster setup with Helm-based deployment for all microservices
GitHub Actions + ArgoCD for fully automated deployment
Redis, Kafka setup and vLLM-based Vertex AI model serving
K6 + SigNoz load testing, Wireguard VPN, Netdata monitoring
Security Incident Response
1. Detection — Netdata Discord Alert
Netdata monitoring agent on the GCP VM detected an anomaly in Nginx web log metrics. Discord webhook fired a CRITICAL alert: "Web log successful = 0%" and "Web log bad requests = 100%".
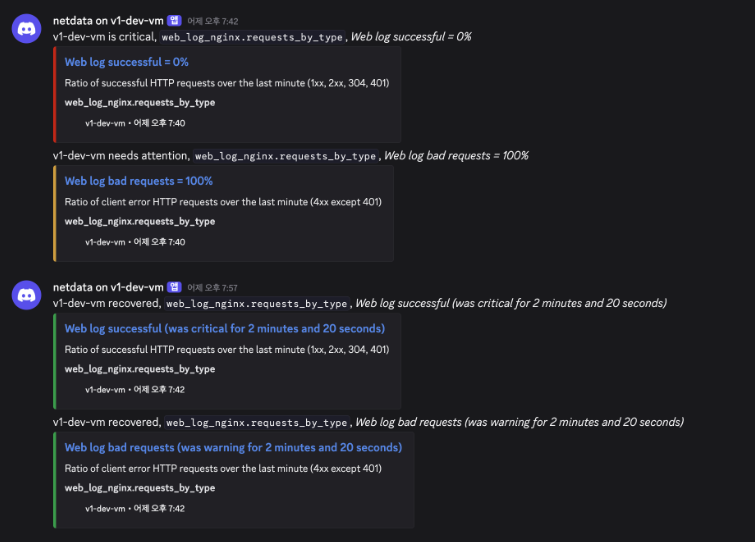
Discord alert from Netdata - Critical notification
2. Analysis — Nginx Access Logs & Netdata Dashboard
Investigated the Nginx access logs and confirmed a targeted scanning attack. The attacker was systematically probing for sensitive files — particularly .env files containing database credentials, API keys, and secret tokens. Requests like GET /.env, GET /api/.env were flooding the server, attempting to exfiltrate environment variables and secrets.
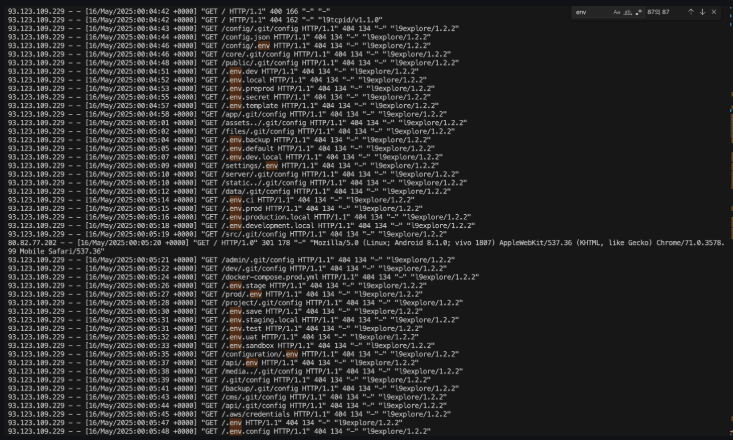
Nginx access logs — .env exfiltration attempts detected
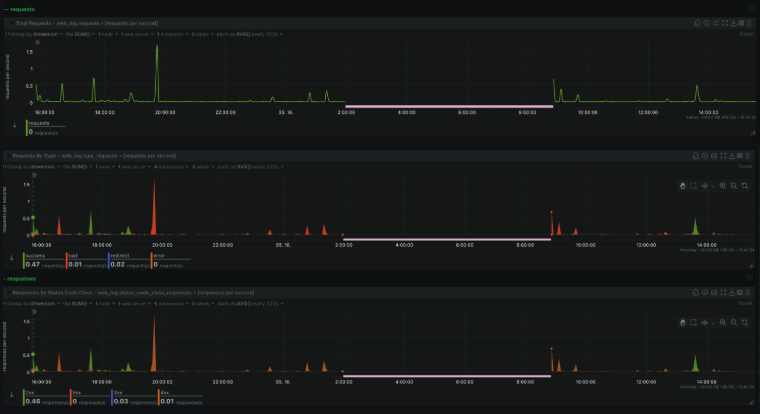
Netdata dashboard - request spike and error rates
3. Resolution — Private Subnet + WireGuard VPN
Redesigned the network architecture from V1 to V2. Moved all backend services (Next.js, Spring Boot, Redis, MySQL) from the Public Subnet to a Private Subnet. Only Nginx reverse proxy remained in the public subnet. Introduced WireGuard VPN for secure developer access to internal services.
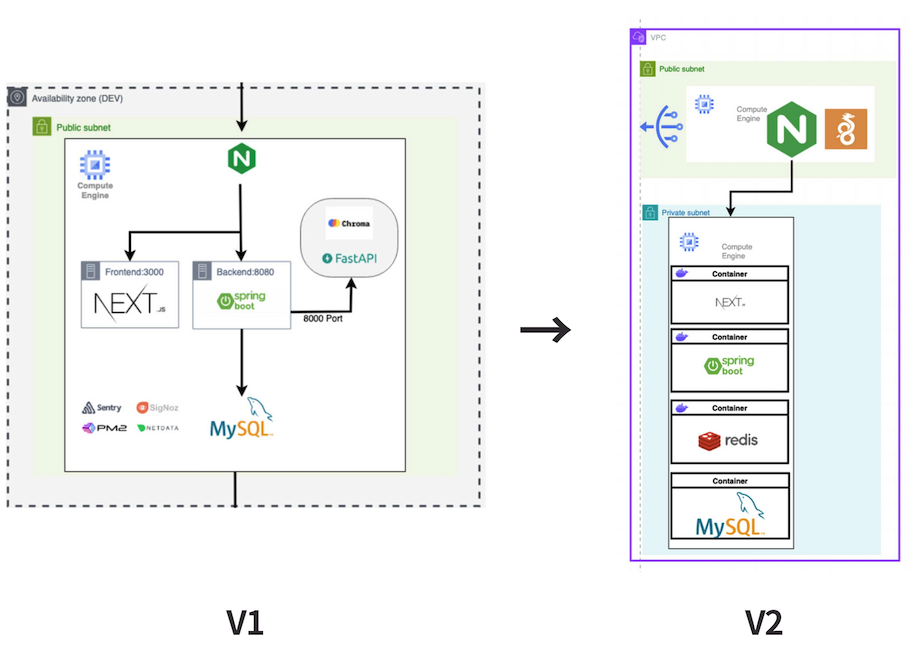
V1 (Public Subnet, all exposed) → V2 (Private Subnet + WireGuard VPN)
4. Result
After migrating to Private Subnet with WireGuard VPN, the attack surface was completely eliminated. Internal services are no longer accessible from the public internet. Only the Nginx reverse proxy handles external traffic, and all developer/admin access goes through the encrypted WireGuard tunnel. No further scanning incidents were detected.
Architecture Evolution
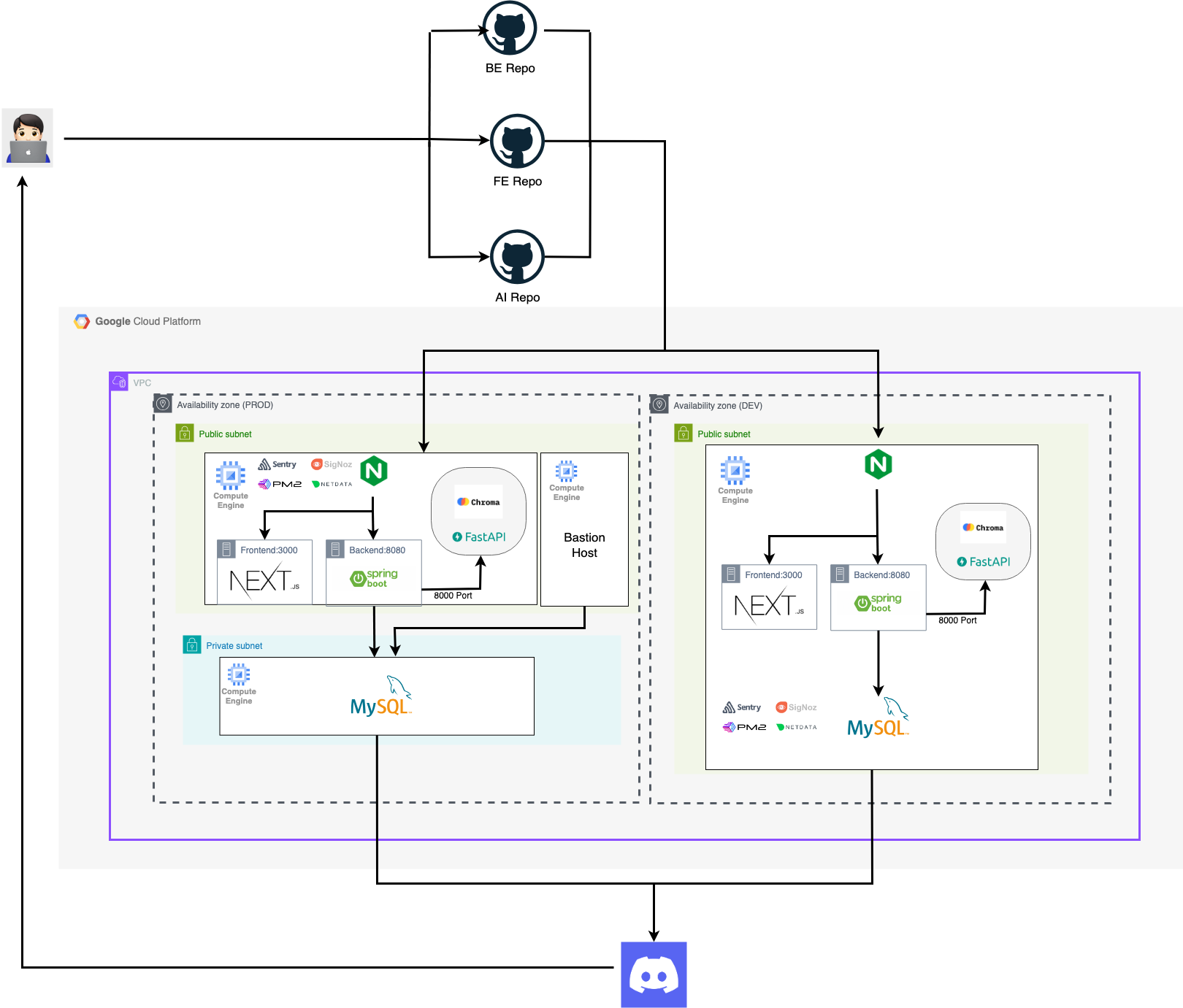
Phase 1: PM2 Manual Deployment on GCP VM
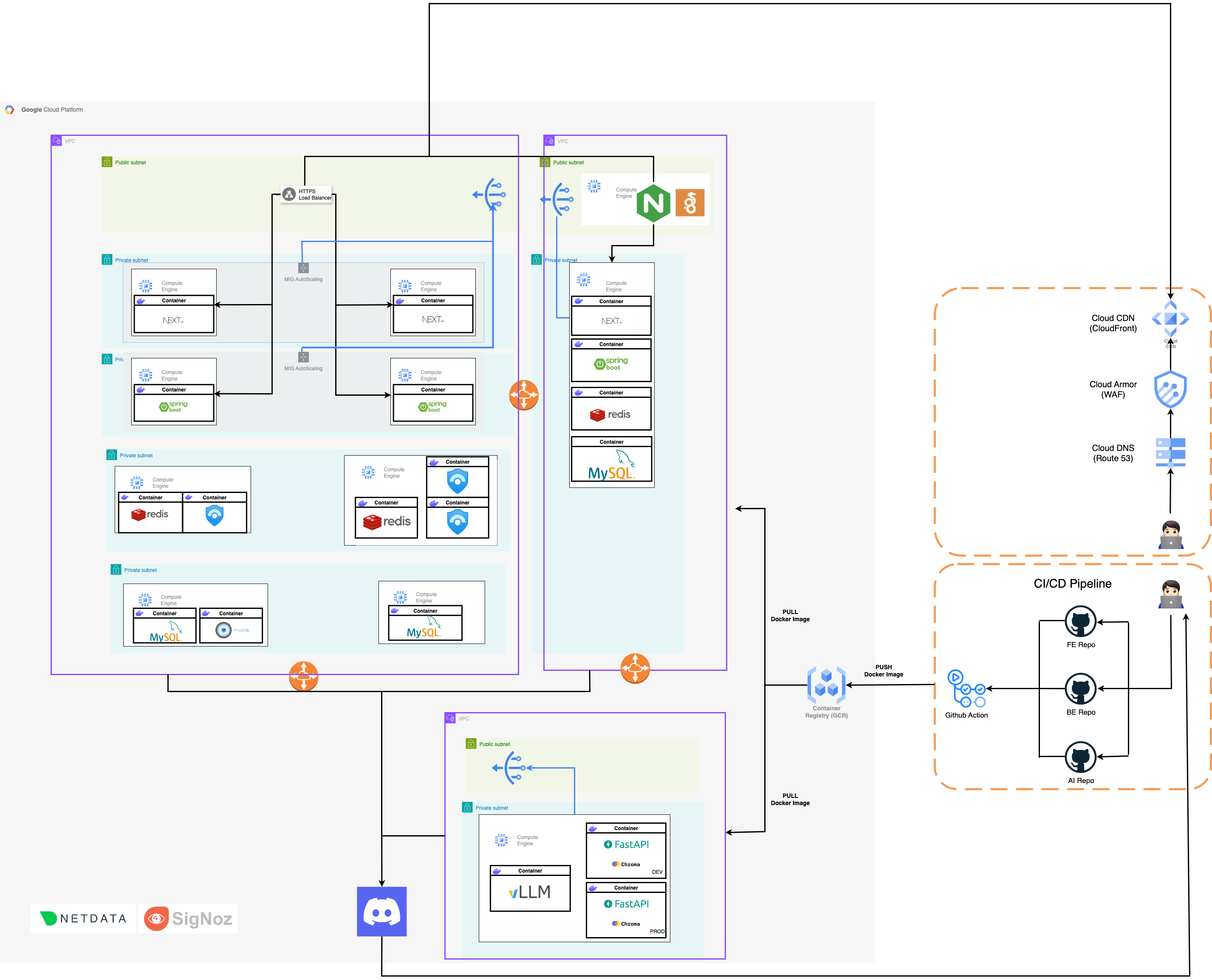
Phase 2: Docker + GitHub Actions CI/CD
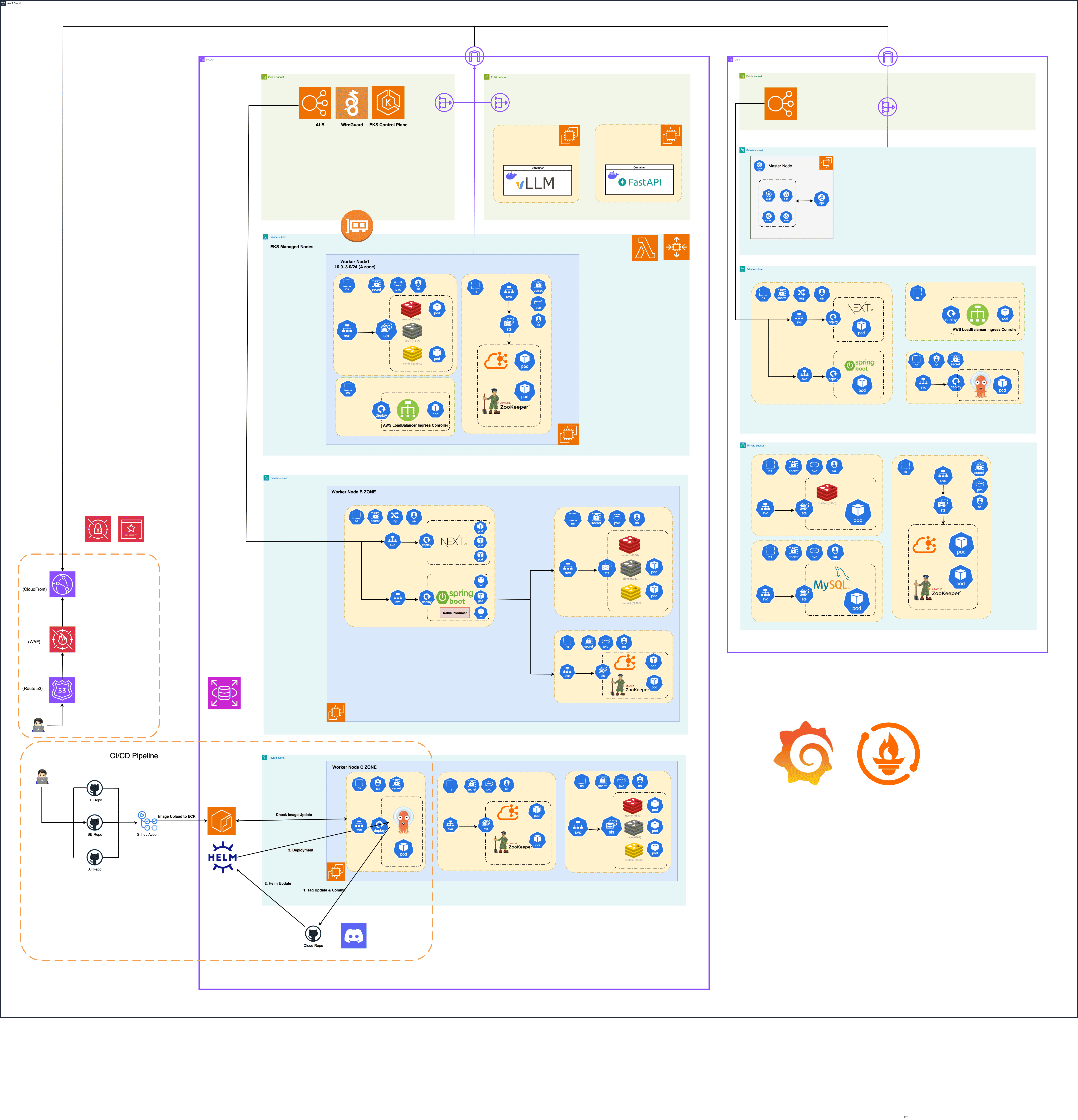
Phase 3: AWS EKS + ArgoCD GitOps